In today’s digital world, businesses rely heavily on their IT infrastructure. Implementing best IT practices is essential to protect data and systems from cyber threats. Here are ten best practices to consider, ranging from regular backups and security measures to disaster recovery plans and regular audits.
Regularly backup important data

Data loss can occur due to many reasons, including hardware failure, cyberattacks, natural disasters, or human error. Regularly backing up important data is a fundamental practice for businesses to ensure that their valuable information is secure and accessible in the event of such scenarios. A robust backup and recovery plan can help businesses quickly restore data and minimize the impact of any data loss incidents, reducing downtime and ensuring continuity of operations.
Regular backups are critical to maintain up-to-date data, and businesses should consider the frequency of backups based on the amount of data generated and the criticality of that data. Many backup solutions offer automated backups to ensure that data is continually being backed up, reducing the risk of human error and providing an added layer of protection.
By regularly backing up their data, businesses can minimize the risk of significant data loss and downtime, providing peace of mind and continuity of operations.
Implement security measures
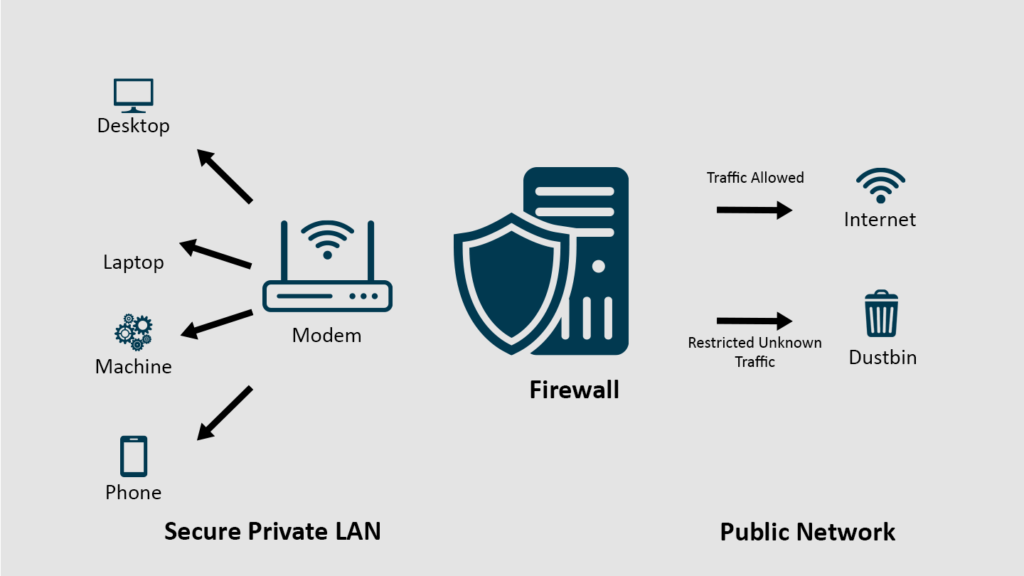
Implementing robust security measures such as firewalls, antivirus software, and intrusion detection systems is critical to protect sensitive business data from cyber threats. These measures work together to safeguard against unauthorized access, malware, and other forms of cyberattacks, reducing the risk of costly data breaches and other security incidents.
Firewalls provide a barrier between internal networks and the internet, blocking unauthorized access and ensuring that only authorized personnel can access sensitive data. Antivirus software can detect and remove malware, spyware, and other malicious software that may compromise business systems. Intrusion detection systems can monitor network traffic, identifying suspicious activity and alerting administrators of potential security incidents.
By implementing these security measures, businesses can protect their sensitive data from cyber threats, reducing the risk of costly data breaches and other security incidents. Regular updates and maintenance of these security measures are also crucial to ensure that they remain effective against emerging threats.
Keep software up-to-date

Keeping software and operating systems up-to-date with the latest security patches and updates is vital to prevent cyber attacks that exploit known vulnerabilities. Regular updates provide protection against emerging threats, ensuring that business systems and data are safeguarded against potential threats and vulnerabilities, and minimizing the risk of cyber attacks.
Train employees on cybersecurity

Educating employees on cybersecurity best practices, such as strong password creation, identifying phishing scams, and safe internet browsing, is crucial to protect business data from internal and external threats. Regular cybersecurity training can help employees recognize and prevent cyber attacks, reducing the risk of costly security incidents and data breaches.
Implement a disaster recovery plan

Implementing a disaster recovery plan is critical to minimize the impact of a major system failure or security breach on business operations. This plan outlines the steps to take in the event of a disaster, ensuring that business systems can be restored as quickly as possible, and reducing downtime and revenue loss.
Monitor network activity
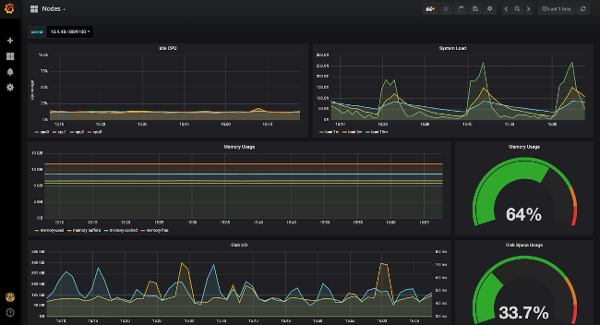
Monitoring network activity is essential to detect potential security breaches, unauthorized access attempts, and other suspicious activities. Regular network monitoring can identify vulnerabilities before they are exploited, allowing businesses to take appropriate measures to prevent cyber attacks and safeguard sensitive data, and reducing the risk of significant security incidents.
Implement access controls

Implementing access controls is critical to limit access to sensitive data and protect business information from unauthorized access. By ensuring that only authorized personnel can access sensitive information, businesses can minimize the risk of data breaches and other security incidents, and maintain the confidentiality, integrity, and availability of critical data.
Maintain hardware

Maintaining hardware such as servers, switches, and routers is essential to ensure that they operate efficiently and effectively. Regular maintenance, including software updates and hardware checks, can prevent system failures, reduce downtime, and prolong the lifespan of hardware components, helping businesses to optimize their IT infrastructure and reduce costs.
Use cloud-based services
Using cloud-based services can provide added security and accessibility to business data and applications. Cloud services can offer enterprise-level security and scalability, while reducing the need for on-premise hardware and infrastructure. This can provide cost savings, enhanced flexibility, and improved business continuity, enabling businesses to focus on their core operations.
Conduct regular audits

Conducting regular audits of IT systems and processes is crucial to identify vulnerabilities and areas for improvement. Audits can assess the effectiveness of security measures, identify compliance issues, and evaluate system performance, providing insights into how to optimize IT infrastructure and reduce the risk of security incidents and downtime.
Get in touch for your IT Services

If you need IT services for your business, get in touch with us. Our team of experts can provide customized solutions to meet your specific needs, whether it’s implementing security measures, managing your hardware, or migrating to the cloud. Let us help you optimize your IT infrastructure and improve your business operations.

